White Papers
-
Root Detection Bypass Appendix
Appendix Instructions The frida-server executable to be run on the mobile device can be found from the following…
-
Exploring Common Vulnerabilities in Self-Driving Cars
Introduction Automated vehicles (AVs) appear to be the future, with more and more automatic features being added to…
-

Introduction to Kiosk Breakout
Introduction A ‘kiosk’ refers to a self-contained computer terminal or device that allows users to access specific applications…
-
Decentralised Applications and Blockchain Security
Introduction With the advent of Web3 and blockchain technology, decentralised applications (DApp) have risen in popularity. Instead of…
-

BIG-IP Remote Code Execution Vulnerability
The Vulnerability For F5’s iControl REST services, a user automatically gets access to REST resources but will need…
-
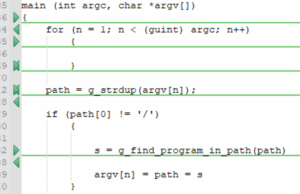
Policykit Exploitation
Introduction A Linux component called PolicyKit (also known as Polkit) is a component used in many Unix-based operating…
-

Supply Chain Attacks: A WordPress Case Study
Supply chain attacks have gained massively increasing attention recently, with the hugely notable cases of SolarWinds in 2020…
-
MouseJacking
Introduction With advances in wireless technologies, it’s becoming common to incorporate wireless technologies into everyday items, an example…
-
Password Cracking
BackStory For in-person infrastructure/network testing, it’s not feasible to carry around large power-hungry GPU servers; but Windows regularly…