Introduction
A ‘kiosk’ refers to a self-contained computer terminal or device that allows users to access specific applications or information. They are typically used in public places such as airports, restaurants, museums, or libraries to provide information, services, or entertainment to users.
Due to their public accessibility, they are often exposed to and operated by a wide-range of users, and so, much of the developmental focus is placed on delivering a streamlined interface to accommodate those with less technological familiarity. Typically operating in retail or hospitality environments, kiosks will usually act as a point of sale system. Thus, it benefits businesses to make them as intuitive and easily operable as possible. This overemphasis on useability often results in an oversight on security, which can be problematic for systems handling transactional information for a large number of users.
This whitepaper will cover some basic kiosk breakout techniques and mitigations on Windows kiosks and future papers will explore breakout techniques and countermeasures on specific platforms such as mobile devices.
Escape Sequences
A trivial ‘example’ kiosk environment might consist of a low-level user logged in with access to a restricted full-screen web browser, locked to a specific page containing the intended point of sale functionality. The goal of any breakout attempt will involve bypassing some of the kiosk’s restrictions to access functionality such as underlying OS features (a file explorer / command prompt) or to simply escape the UI restrictions in place. In the case of a locked-down web browser, these breakouts could allow for navigation to arbitrary URLs permitting an adversary to have the kiosk display an attacker controlled page, visually identical to the legitimate interface, but with malicious functionality such as credential harvesting.
For the sake of ease of use, many publicly exposed kiosks permit input via a touchscreen, offering simple binary ‘point and click’ interactions. However, it’s highly likely that an on-screen keyboard will be displayed when user input fields are selected, allowing for more complex input. Keyboards and other input devices may also be attached to kiosks with physically exposed USB ports. If keystrokes are able to be sent to the device, then various hot-keys and key combinations can be leveraged to gain additional control over the system. For example:
CTRL + N ← Will open a new window in most desktop browsers. This window may be a fully functional browser instance with full access to the toolbar, navigation buttons and browser settings. From this point it is often trivial to launch a file explorer in most OS’s and a subsequent command prompt.
CTRL + SHIFT + P ← Can be used almost universally across browsers to bring up a print dialogue. A file explorer can then be accessed by navigating to ‘Find Printer’ in Windows 10 or by using CTRL + P → ‘More Settings’ → ‘Print Using System Dialogue’ → ‘Find Printer’. In windows 11. Alternatively, selecting ‘save as PDF’ → ‘Print’ will also produce a file explorer. This file explorer alone can be enough to constitute a compromise of confidentiality and integrity by allowing the user to browse the file system, open files (right-click → Open), as well as delete and rename files.
If standard hotkeys are disabled, it may be possible to use the F1 function key to navigate to the default help page. In MS Edge this page includes a clickable ‘print’ option under the ‘Privacy Statement’ towards the bottom of the page which will open a file explorer. Similarly, in chrome, the default help page includes download links which can be used to achieve the same outcome.
From these default help pages, it is often possible to reach almost any publicly indexed webpage by recursively following links to ‘google’ for example, and then using the search engine to visit a desired page. This is particularly useful when the navigation bar is disabled.
CTRL + S ← Will cause many browsers to save the current page to the local filesystem and will prompt the user for a location by spawning a basic file explorer.
CTRL + O ← Will open a file in the browser, producing an explorer for file selection.
CTRL + J ← Will open the downloads page, which contains options to open up a full file explorer.
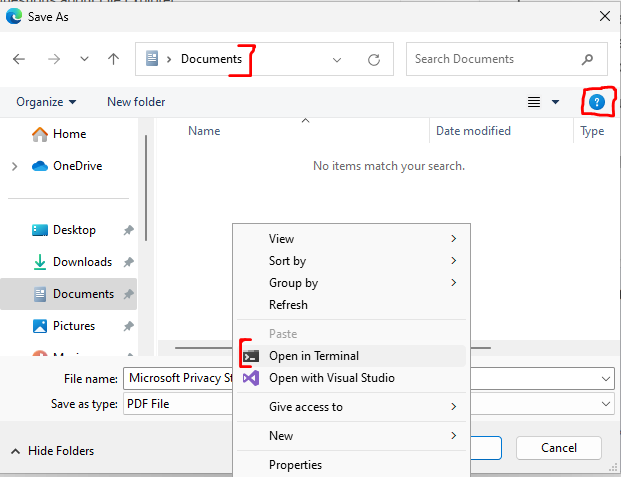
Once a file explorer has been obtained, a command prompt can be opened in Windows 11 by right-clicking inside of a local directory and selecting ‘open in terminal’. In windows 10 an instance of powershell can be launched from a full file explorer by going to ‘File’ → ‘Open with Powershell’. Additionally, the file path navigation bar can be utilised in Windows 11 and below to open and pass any arguments to executables in the systems path E.G: cmd.exe, taskmgr.exe, calc.exe, winword.exe etc.
Typing the string ‘shell:’ followed by the name of a special folder can be used for redirection to various windows locations such as the system32, cryptoKeys, and cache folders, as well as locations without an explicit path such as ‘This PC’, ‘OneDrive’ and ‘Recents’. The full list of shell:commands for Windows XP through to 11 can be found here: https://www.winhelponline.com/blog/shell-commands-to-access-the-special-folders/
Typing the ‘control’ keyword into this same navbar can be used to launch the control panel which may allow for further system enumeration and modification of some system settings.
If these methods are unsuccessful, the help icon can be another vector inside of the explorers UI. Clicking this (or pressing F1) will open up a new (potentially un-restricted) browser window with access to the bing search engine.
If a physical keyboard can not be connected to the kiosk and the keyboard used to populate input fields does not contain buttons such as CTRL, Function or Windows Keys, it may be possible to obtain a more complex keyboard either using sticky keys, (even rudimentary on-screen keyboards will often contain the shift key) or by obtaining a basic file explorer with a point-and-click method and accessing the control panel via the navbar and navigating to ‘Ease of Access Center’ → ‘Start On-Screen Keyboard’.
Further to this, operating system hotkeys should also be tested. These are often disabled but can be particularly powerful for escaping heavily locked down interfaces if permitted. CTRL+ALT+DEL for instance, can provide a means for accessing task manager, locking, shutting down or power-cycling the device (denial of service), or even changing the current user’s password. The Windows Key, ALT+TAB, Windows+D, Windows+TAB may provide an escape for applications locked in full-screen mode and offer access to the underlying GUI if explorer.exe is running on Windows devices.
In cases where the application breakout is successful, but access to command prompt and other system shells are blocked, it may be possible to achieve code execution via native OS scripts such as .bat, .ps1, .vb and Windows Script Host supported languages. If .NET framework is installed then ‘msbuild’ can be used to compile and run C# programs offering another vector for code execution. Microsoft Word macros can also be used to achieve the same result, however, code obfuscation techniques may have to be applied if the device is using an AV solution, regardless of the chosen scripting language. Depending on the machine configuration these scripts may be buildable on the device itself or may require infiltration via USB or web-browsers.
Other Attack Vectors
Physically disconnecting a kiosk from its network and providing an alternative form of connectivity (via a USB Wi-Fi dongle or attacker controlled ethernet bridge) may allow network based restrictions such as firewall rules, HTTP proxies and remote management software to be bypassed. Power-cycling devices at key stages during the boot process may invoke the Windows Recovery Environment (WinRE) which can be used to gain full local-admin access to the system on Windows Vista through to Windows 11. Common and default passwords often make it to production environments which can also be used to gain administrative access.
Mitigations
An attacker’s main advantage in kiosk breakout scenarios is their physical access to the device. This can allow them to infiltrate malicious files, imitate human input devices, power-cycle the device, tamper with network connectivity and exfiltrate sensitive data. Thus, kiosk devices should be deployed with maximum physical security to discourage tampering. Sensors may be used to detect physical break-in attempts and a trusted anti-virus solution should be implemented to prevent the infiltration of malicious files and programs such as keyloggers. Whilst in its kiosk configuration, the device should not communicate with any newly connected devices and all keyboard hotkeys should be disabled and access to any system settings, properties and shells blocked. Due to the number of angles available to an attacker it’s important to rely on defence in depth and integrate multiple layers of security. For instance, firewall restrictions imposed by the network via intermediary devices should also be implemented at the device level; and if the physical security of the kiosk is compromised then additional security mechanisms should be in place, such as local policies that prevent the device from connecting to unauthorised networks. Hardware level encryption should also be considered to protect sensitive data stored on the disk, in addition to the previously mentioned physical protections. Finally, regular security auditing should be carried out to identify new vulnerabilities, especially if proprietary software is in use.
Whilst these mitigations will apply to most devices, particular attention should be given to defence in depth practices, so that additional protections are in place should a physical compromise occur. It’s also important for system settings and administrative tools such as CMD and Powershell to be locked down. Security through obscurity (I.E. attempting to restrict access by omitting certain buttons and GUI features) should not be relied upon as there are numerous ways to circumvent these restrictions. As previously mentioned, kiosks are particularly sensitive due to their physical accessibility and should be regularly monitored, maintained and assessed for evidence of compromise.
References
- https://www.winhelponline.com/blog/shell-commands-to-access-the-special-folders/
- https://book.hacktricks.xyz/hardware-physical-access/escaping-from-gui-applications
- https://blog.nviso.eu/2022/05/24/breaking-out-of-windows-kiosks-using-only-microsoft-edge/
- https://www.youtube.com/watch?v=blNSJxk9PtE
- https://www.kiosksimple.com/blogs/news/kiosk-hacking