Introduction
On the 26th of September 2024, Simone Margaritelli, also known as ‘Evilsocket’ disclosed, publicly, four vulnerabilities within the Common Unix Printing System (CUPS) that, combined, can allow an unauthenticated attacker to gain Remote Code execution on a network accessible computer.
What is it?
This exploit allows an attacker to forcibly advertise a printer across a network to any machine running CUPS. When a victim attempts to print to this printer, a PostScript Printer Description (PPD) file will be created on the victim’s computer that will then execute code remotely.
Some background on CUPS and IPP
This vulnerability relies on CUPS being in use on the victim’s machine, but what is CUPS? The Common Unix Printing System began development in 1997 as a modular printing system for UNIX based systems utilising the Internet Printing Protocol (IPP), although initially designed to be used with the Line Printer Daemon Protocol (LPD).
CUPS allows a computer to act as a print server, managing print requests for client computers and sending them to the relevant printers. CUPS also utilises PPD files to store the descriptions of printers, their capabilities, resolutions they can print at, whether they can print in colour, and so on. PPD files are an important part of the exploit, as will be discussed later.
The Internet Printing Protocol (IPP) is a protocol specifically designed for the communication between printers and client devices. It began development in 1996 and was initially developed as a joint venture between American software company Novell and printing company Xerox, as the Lightweight Document Printing Application (LDPA). They were joined in this development by HP and Microsoft who had begun working on new print services for windows 2000, eventually leading to IPP/1.0 being published in 1999 as a series of experimental RFC documents.
IPP relies on HTTP and communicates to servers in much the same way that a home computer may talk to a website or API, this means that IPP can integrate all of the security mechanisms present in these requests can be used to send printing jobs, add new printers, query a printer’s capabilities, or query the status of a print job across the network, among other things.
What vulnerabilities does this exploit utilise?
As previously stated, this exploit relies on four separate vulnerabilities in various components of the CUPS service, including: cups-browsed, a daemon used to browse the network for remote CUPS queues and IPP printers, ‘libcupsfilters’, a library that provides filter functions for IPP server attributes, ‘lippd’, a library for handling PPD files and ‘cups-filters’, a library for converting input formats to printable formats.
CVE-2024-047176
This vulnerability, in the cups-browsed library, will trust any specially crafted User Datagram Protocol (UDP) packet sent to port 631 in order to trigger a ‘Get-Printer-attributes’ IPP request to an attacker-controlled URL. The result of this is that any UDP packet sent to port 631, containing a payload in the following format causes the CUPS server to connect to that server as if it were a printer without notifying the victim, advertising it on the victim’s computer:
‘a 0 3 http://<REMOTE_SERVER_ADDRESS>:<PORT>/printers/directoryName’
CVE-2024-47076
‘Libcuspsfilters’ contains code relating to the deprecated ‘cups-filters’ package. The ‘cfGetPrinterAttributes5’ function completely lacks any sanitisation on the IPP attribute fields returned from an IPP server, allowing an attacker to inject data into these fields and affect the rest of the IPP server. This lack of sanitisation allows the data to be passed into the next important function ‘ppdCreatePPDFromIPP2’.
CVE-2024-47175
‘Libppd’ is a library within CUPS used for legacy PPD support and contains the function ‘ppdCreatePPDfromIPP2’. This function does not sanitise IPP attributes when creating the PPD buffer. Consequently, attacker-controlled data can be written to the PPD file that’s created when a printer is added to the CUPS server.
CVE-2024-47177
The ‘foomaticRipCommandLine’ function within the ‘foomaticRip’ filter allows for any value to be passed to it via PPD file and executed as a user-controlled command. This allows the code injected into the PPD file via the previous 2 vulnerabilities to be executed.
How does it work?
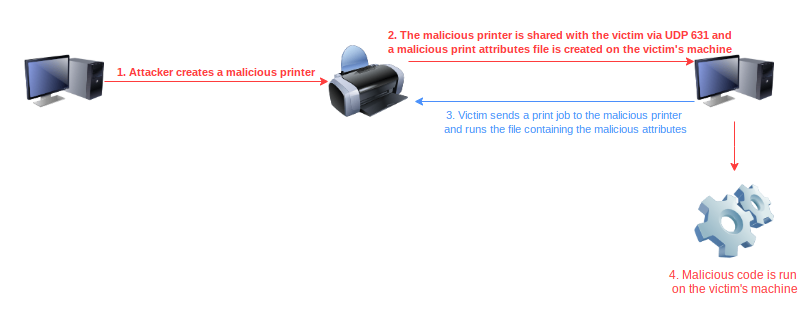
The vulnerability can be broadly split into two parts: the initial vector and foothold facilitated by CVE-2024-4716 and the RCE facilitated by CVE-2024-47016, CVE-47175 and CVE-47177.
RCE Attack Chain
The attack chain to RCE using this exploit is as follows:
- Utilising CVE-2024-47176 to send a UDP packet with a payload containing a URI pointing to an attacker controlled IPP server.
- The specially crafted attacker controlled IPP server returns an unsanitised IPP attribute string, used to inject PPD directives into a temporarily created file.
- As soon as the victim sends a print job to the attacker-controlled printer, the stored PPD directives are run, containing the injected command and as such, this causes RCE to take place.
Video Demo
The Impact
There are a multitude of potential impacts associated with unauthenticated RCE, this could be anything from a full-scale ransomware attack, mining for crypto currency, or the exfiltration of sensitive company data; nothing is ‘off the table’ when it comes to RCE. However, the attack vector, in conjunction with the social engineering needed to successfully carry out an attack using this vulnerability increases the complexity of a successful attack substantially. Additionally, a patch has been released for this vulnerability, which further lowers the likelihood of this being successfully exploited in the wild.
Remediations
There are a couple of potential ways to remediate this; the initial advisory urges the reader to remove any CUPS-related service, but it may be advisable to instead use the patch provided by Ubuntu. This patch was released by Canonical on the 26th of September 2024.
Additionally, if the older version of CUPS is required, filtering packets on UDP/631 using a firewall is an advisable remediation for a defence in depth approach.
Lessons Learnt
This exploit poses a significant risk to both organisations and their customers. Ensuring that all important patches are applied as soon as possible after their release, can be the first step to preventing attackers from compromising business critical systems. It should also be noted that it is important not to get caught up in the speculation surrounding new vulnerabilities, acting methodically can reduce the risk of causing conflicts by disabling or replacing mission-critical software.